The best way to protect users in Azure is to enable 2 factor authentication, but this can take time to setup and enforce for all users. One of the extra checks you can perform is to look at the Azure sign-in logs using MS Graph. This will give you a list of logons to all Azure services, showing the username, country and IP. Using this information Microsoft provide alerts for suspicious logons, for example where a logon was detected from a country not normally seen.
These alerts can be very useful but oddly this only works where the records shows an IPv4 address, if the user logged on using an IPv6 address it will not detect the country. So using a PowerShell script we can do the following:
• Report on all users logged in successfully in a 24 hour period.
• Do IPv6 country lookups, something Microsoft does not currently do.
• Exclude certain countries from the report, eg you might not be interested in logons from your home country.
• Send an alert email if suspicious logons are detected.
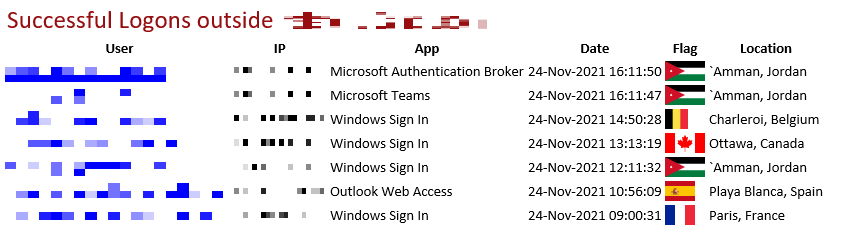
↑ Alert email to show logons from certain countries.
For IPv6 lookups we can use IP-API.com to get their location:
$iplookup = Invoke-RestMethod -Method Get -Uri "http://ip-api.com/json/$r_ip"
$countryname = $iplookup.country
$city = $iplookup.city
$countryname = $iplookup.country
$city = $iplookup.city
For the country's flag you can download all of them through GitHub and then reference them via their 2 letter country code (ISO 3166-1).
Finally we can keep track of successful and failed logons per day by outputting to a log file which can then be read by the PowerShell script and displayed in a HTML page. Each bar links to an Excel report listing all the logons.
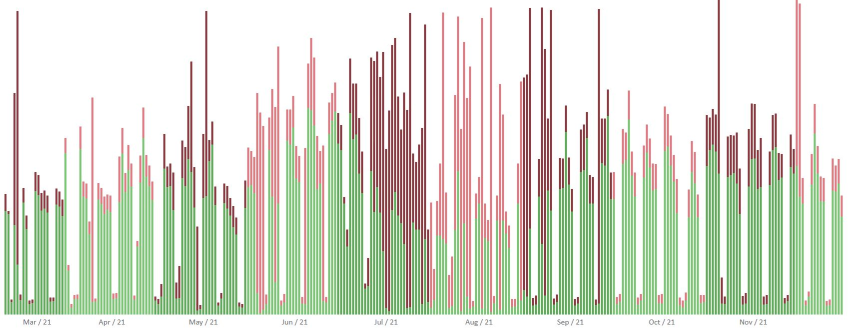
↑ Table of all logons per day.
 Graph and PowerShell Blog
Graph and PowerShell Blog