Linked Article: Further troubleshooting Integrated Apps
Until recently I let my cloud admin handle Outlook add-ins aka Integrated Apps. The policy was to block all apps entirely to reduce the number of potential data leaks and security holes.
Now though, I've been asked to deploy the Microsoft add-in 'Report Phishing' and configure the options.
The first thing to check is the Exchange User Policy under EAC - Roles - User Roles. The default role should have these settings enabled, but as I said previously we blocked all access, so here I have created a new policy and assigned it to test users.
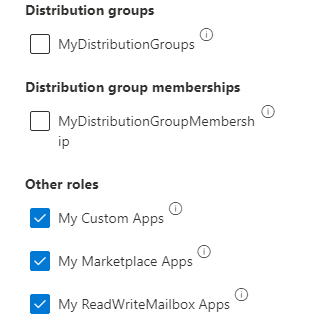
↑ New policy set up with permissions to view and install add-ins.
Next, we need to make the add-in available for users. We'll need the 'Exchange Admin' and 'Application Admin' roles activated for this if you are not a 'Global Admin'. Once this is done we go to Microsoft 365 Admin Center - Settings - Integrated Apps and add the app by searching for it under 'Get apps'.
The steps are self-explanatory, you can decide to publish the add-in for yourself, a group of users, or everyone. What it doesn't show is how the app is deployed, by default it will become 'Available', but this is only viewable on the old AdminPortal page.
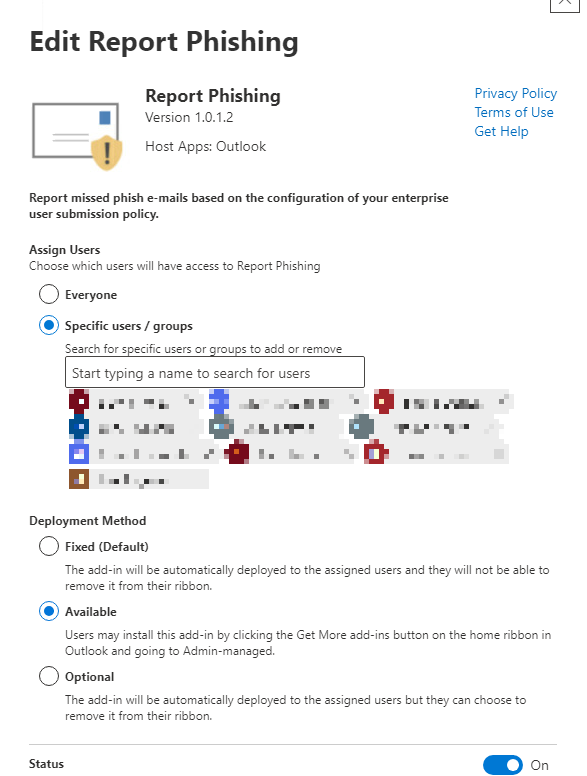
↑ We can see here our app is set to 'Available', so users must install it themselves.
With the app deployed and installed by users, we can now focus on setting up what the add-in does when a user reports a mail within Outlook. This is set under Microsoft Defender - Settings - Email & collaboration in O365. First, we define that we want to use the Microsoft add-in and not a 3rd party.
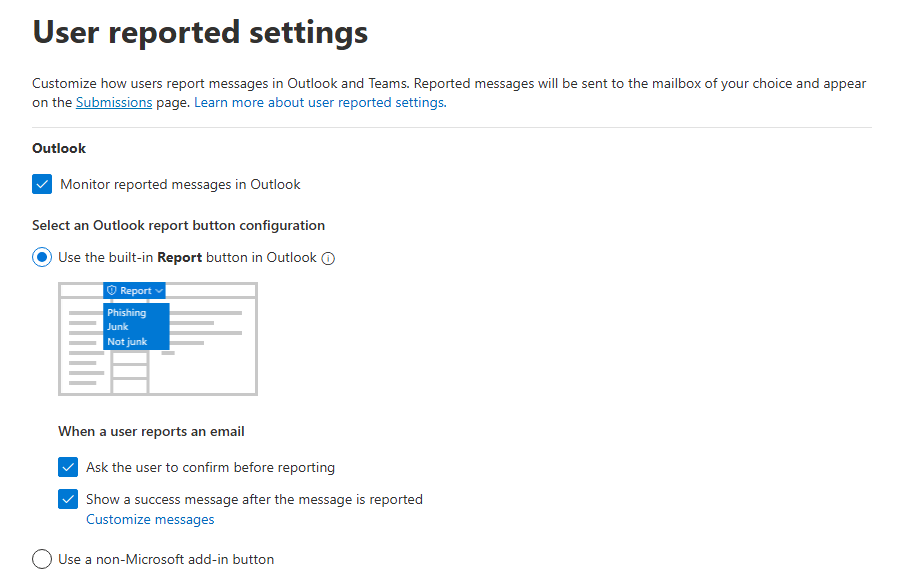
↑ We have selected to use the Microsoft add-in.
Then we can define what happens when the message is reported.
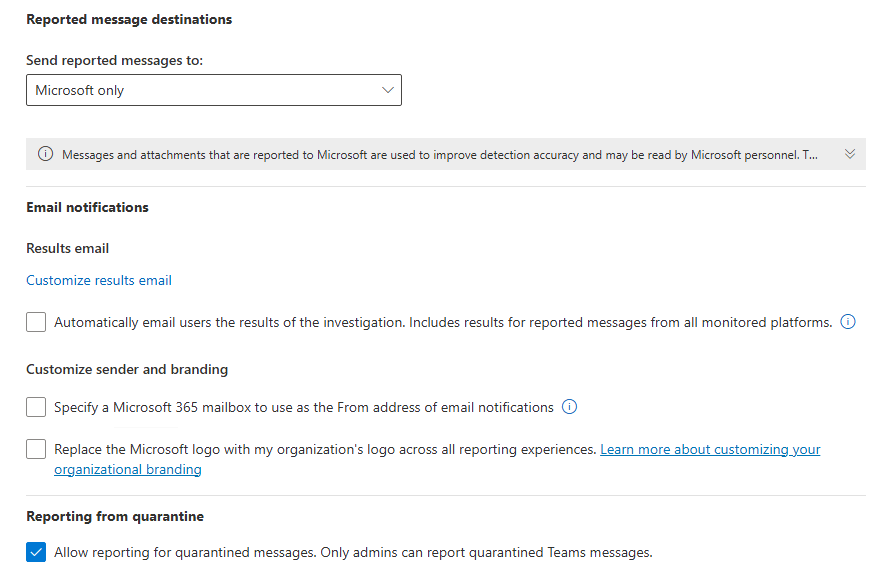
↑ We can send the email to Microsoft for analysis or we can add it to our mailbox, or both.
Block Users from Installing Third Party Apps
When any app is deployed by an admin, it appears to overwrite any settings in Outlook that blocks the store. This seems to be a new functionality from Microsoft in 2024. To stop users from installing third party apps you should get your Global Admin to block this setting under M365 Admin - Integrated Apps - Deployed Apps (setting cog).
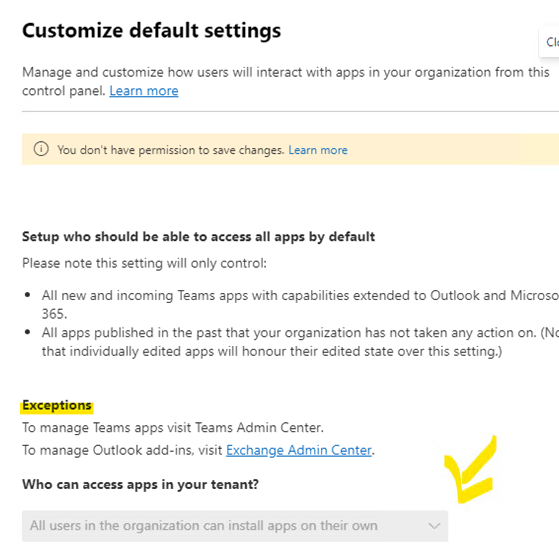
↑ Block 3rd party apps under M365 Admin - Integrated Apps - Available Apps (settings cog).
 Graph and PowerShell Blog
Graph and PowerShell Blog